Oauth2 and Google services
OAuth 2.0 is an open authorization framework that allows applications to access the resources of a user on a given service. When using OAuth 2.0 with Google services, you can obtain access tokens that enable your application to interact with various Google APIs on behalf of the user. To use OAuth 2.0 with Google services, you’ll need to perform the following steps:
-
Create a project in the Google Cloud Console: Go to the Google Cloud Console (https://console.cloud.google.com) and create a new project. This project will represent your application.
-
Enable the necessary APIs: Within your project, enable the specific Google API(s) that your application needs to access. For example, if you’re building a calendar application, you would enable the Google Calendar API.
-
Set up OAuth consent screen: Configure the OAuth consent screen to specify the information about your application that will be presented to users when requesting access. This includes the application name, logo, and any requested scopes.
-
Create credentials: In the Google Cloud Console, create OAuth 2.0 client credentials for your application. You can choose between different types of credentials depending on your application’s requirements (e.g., web application, mobile app, etc.). During this process, you’ll be asked to provide a redirect URI, which is the endpoint where the authorization server will redirect the user after authentication.
-
Implement the authorization flow: Depending on the type of application you’re building, you’ll need to implement the appropriate authorization flow. Common flows include the authorization code flow and the implicit flow. The authorization flow involves redirecting the user to Google’s authorization server, where they will be prompted to grant your application the requested permissions.
-
Obtain an access token: Once the user grants permission, your application will receive an authorization code or an access token directly, depending on the flow you implemented. You can exchange the authorization code for an access token by making a request to Google’s token endpoint.
-
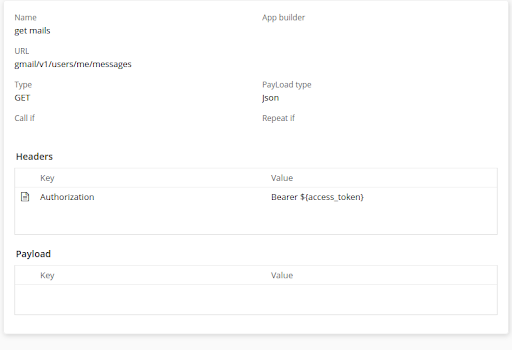
Use the access token: With the access token, your application can make authorized API requests to Google services on behalf of the user. Include the access token in the Authorization header of your requests, following the OAuth 2.0 Bearer token scheme.
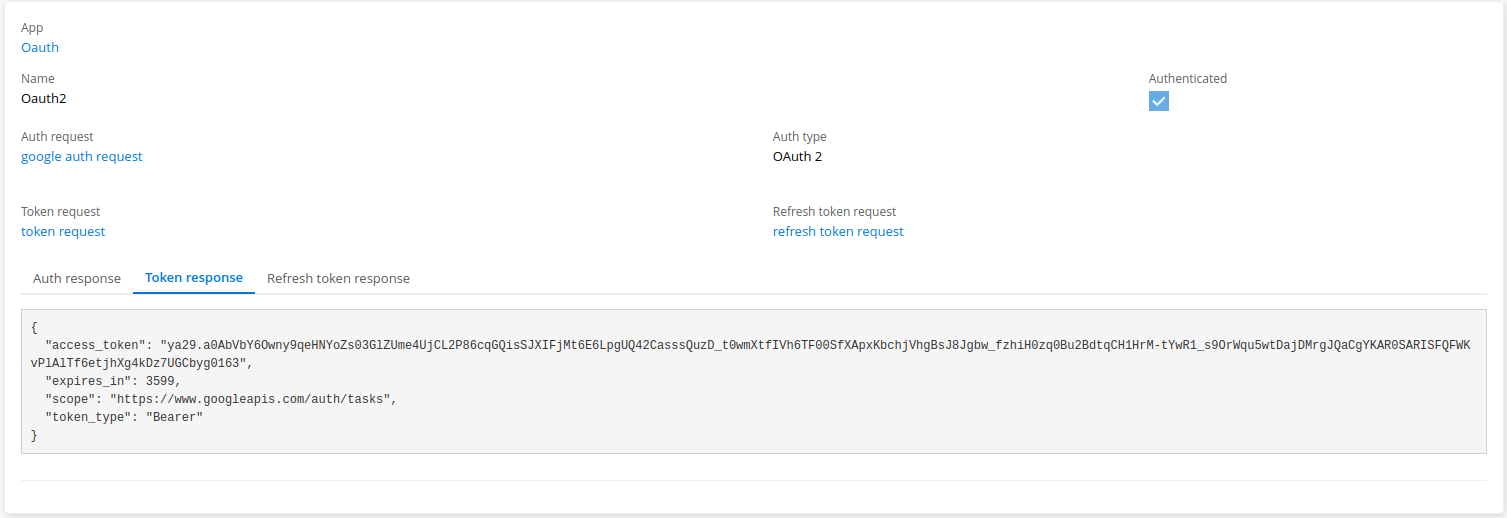
Authentication
We have to create an authentication to connect with Oauth2 google protocol .
it’s an oauth2 authentication , we need to provide a request authentication to get the code of authentication , it is needed to get the token . also we need to provide a token request to get the token , and create a refresh token request
Authentication request
The authorization request typically involves the following steps:
-
The client application (the third-party app) redirects the user to the authorization server’s authorization endpoint URL, with the following parameters:
-
Provide a client_id , the unique identifier of the client application
-
Add redirect_uri: the URL to which the authorization server will redirect the user’s browser after the authorization is complete
-
Specify the response_type the value should be "code", indicating that the client application is requesting an authorization code
-
The authorization server authenticates the user and asks for their permission to grant the requested access.
-
If the user grants permission, the authorization server generates an authorization code and redirects the user’s browser to the client application’s redirect_uri with the authorization code appended as a query parameter.
-
The client application receives the authorization code and can then use it to request an access token, which will allow it to access the protected resources on behalf of the user.
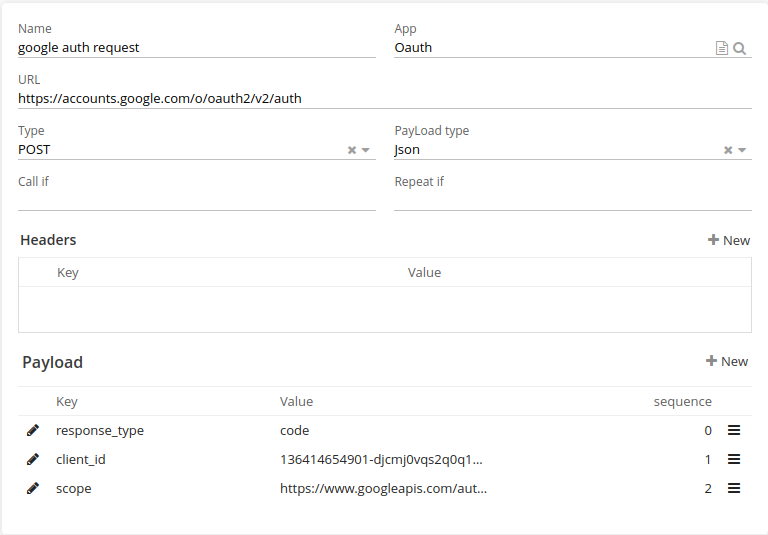
| It’s important to note that the authorization code should be kept confidential , also for redirect_uri it’s not important to mention here. For the client id you can configure your Google console developer account to get your client_ID . You can do the configurations with this link : https://console.cloud.google.com |
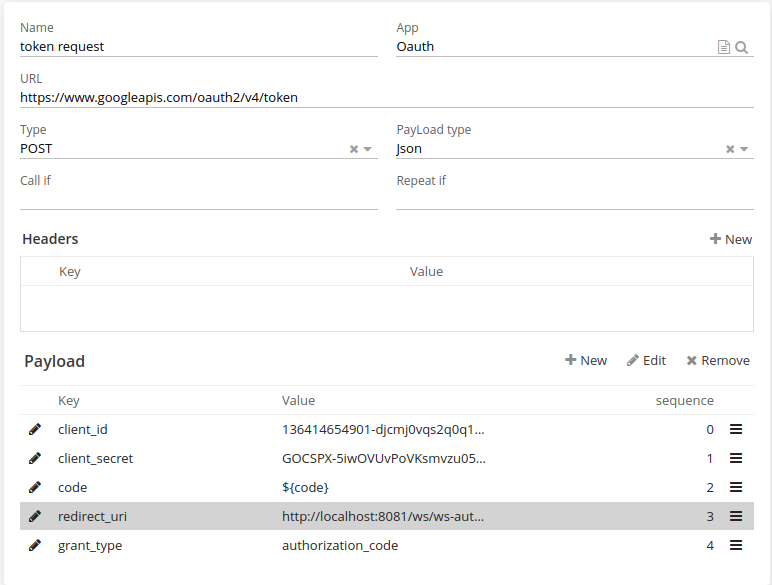
Token request
To make the second request to get the token, you’ll need to send a POST request to Google’s token endpoint (https://oauth2.googleapis.com/token) with the following parameters:
-
grant_type : set to "authorization_code"
-
code : set to the authorization code obtained in step 1
-
redirect_uri : set to the same value used in the authorization request
-
client_id : the ID of the Google Cloud Console project
-
client_secret : the secret key of the Google Cloud Console project
Refresh token request
To request a refresh token, you’ll need to include the access_type parameter in the initial authorization request to Google’s authorization server. This parameter should be set to "offline", which indicates that you’re requesting a refresh token along with the access token.
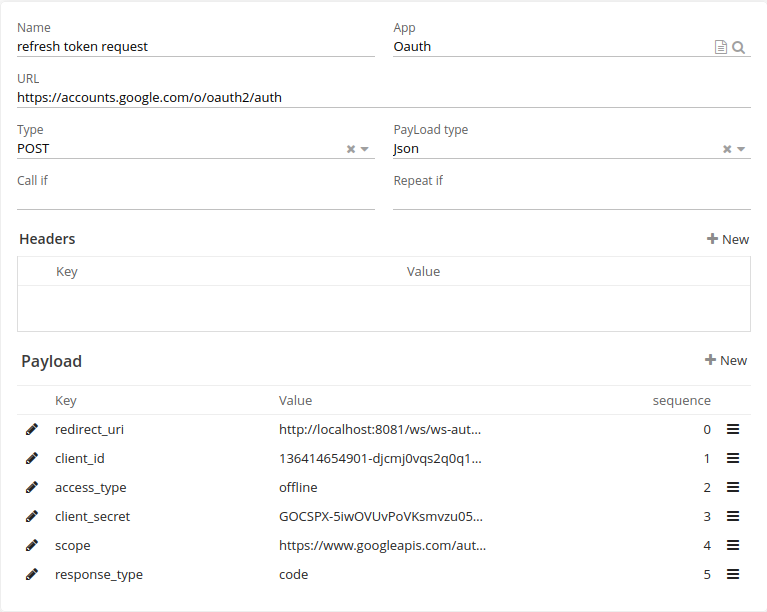
| When we click on the authenticate button , you can see the result on the tab panel bellow . every panel correspond to the result of the execution of any requests of those three . |